CLAS IT Connections
Article Category: <span>Security</span>
Locking the Padlock: How to ensure your website connects to users securely.

HTTP vs. HTTPS Http stands for Hypertext Transfer Protocol. It’s essentially a method of communicating information between web servers and clients. When we add the “S” onto the end, not surprisingly, we’re securing the connection. If you go to a bank or eCommerce website, you will most likely see that the URL leads with HTTPS
Read more "Locking the Padlock: How to ensure your website connects to users securely."
Skip the Phish

phish-ing – /’fiSHiNG/ – noun. The fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers. A day does not go by without a phishing attack against university accounts. According to UFIT, last year alone there were over
REBOOT!!!
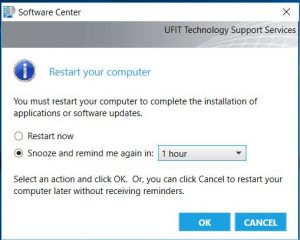
As we roll out Windows 10, the need to reboot your computer at least once a week becomes more important. Microsoft upgrades their core Windows operating system now on a regular basis very much like Apple has been doing. Windows computers must be rebooted in order for those updates to occur. Upgrades are pushed out
Two Factor Authentication (2FA)

DUO Two factor authentication was rolled out in the spring and has been in testing here at UF for almost a year prior. The way DUO works is that after you enter your password on certain resources, like myUFL and the UF VPN, you will be asked for a second method to verify your identity
Passwords, Two Factors, and Fobs? Oh My!

Passwords are everywhere in our lives these days. They are important because of what they are intended to protect our information.
Gated Parking: A Beginners Guide to Getting Moved to the Top of the Queue

I have just discovered a way to get moved to the top of the queue for a Gated Parking Decal and I can get that decal at half the normal price!
Read more "Gated Parking: A Beginners Guide to Getting Moved to the Top of the Queue"
How Vulnerable Is Your Data?

When we think of data privacy, the first thought is likely about how we as individuals are vulnerable to having our information land in the hands of someone that should not have access to it. All too frequently we hear of high-profile data breaches that have occurred everywhere from federal and state agencies to retailers,
Do You Need Adobe Flash and Java?

Adobe Flash and Java are add-on software packages, plugins, which provide additional functionality, such as the ability to watch videos or listen to music, from within the web browser. Examples of sites that use this are YouTube, SoundCloud, most online games, and even some campus sites such as E-Learning still have ties to flash or
Free Services and Apps: Nothing is Ever Free

“There ain’t no such thing as a free lunch!” That phrase featured prominently in Robert Heinlein’s novel The Moon is a Harsh Mistress. Many organizations — some respectable and some that have no hesitation to squeeze whatever they can out of us — are offering seemingly free services or products that are a way to
Mobile Device Encryption

We would like to remind everyone that all mobile computing and storage devices that house UF data, regardless of ownership, must be encrypted.